The "Demonic" Browser Wallet Vulnerability: Explained
A walkthrough of the significant vulnerability exposing key material in popular browser-based wallets.
Today, Halborn Security announced a significant vulnerability exposing key material in MetaMask, Coinbase Wallet, Brave, Phantom, and many other browser-based wallets.
Security researchers at @HalbornSecurity have disclosed a wallet vulnerability that affects a small segment of users across many browser-based wallets, including MetaMask.https://t.co/2tBl8BfISA
— MetaMask 🦊💙 (@MetaMask) June 15, 2022
1/ 🧵
Thankfully, Tally Ho wasn't impacted by this vulnerability. When we decided to build a new web extension wallet from scratch, we took the opportunity to rethink our extension architecture. We decided to avoid any new tab or window activity that wasn't required by a dApp — the security implications weren't clear, and we didn't want to take the risk.
The MetaMask and Halborn teams were quick to inform wallet dev teams and helped to coordinate a response across the entire community.
Unfortunately, this vulnerability has been live for a long time. If you've ever imported a recovery phrase in an impacted browser extension before March 2022, your keys might have been exposed to malware on your machine.
How is this possible?
MetaMask's security model
Like many wallets, MetaMask can generate or import a recovery phase. Your recovery phrase can be used by you—or anyone else!—to recover your funds and access your wallet across multiple devices. All private keys are derived from this phrase.
Your wallet only needs access to your key material when it needs to sign transactions. The rest of the time, MetaMask keeps that material encrypted using the password you provided, preventing any sensitive material from being saved to disk.

However, if your key material is saved to disk, unencrypted, other programs can access it— as well as anyone else with access to your computer.
Browsers are Swiss Cheese
In their constant race for market share, browsers are notorious for prioritizing user features over security.
Over time, these tradeoffs have led to a more and more dangerous browsing experience. Today, maintaining privacy and isolation in a browser is incredibly difficult.
Many popular browsers (Chrome, Firefox, Brave, Opera, etc.) save all input fields on disk, unencrypted, by default. The reasoning behind this is to make restoring tabs easy after shutdown.
In contrast, most browser extension wallets today have an onboarding flow that opens in a new tab. MetaMask introduced this feature years ago, thus creating the concept of a browser extension wallet. The unfortunate reality of this, however, is that even the entirely new tabs aren't protected from common browser behavior.
This means that every typed recovery phrase is saved to disk, unencrypted.
The vulnerability
A story told through screenshots: An example of the vulnerability in action using Coinbase Wallet before the vulnerability was patched.
First, here's the onboarding flow for Coinbase Wallet.
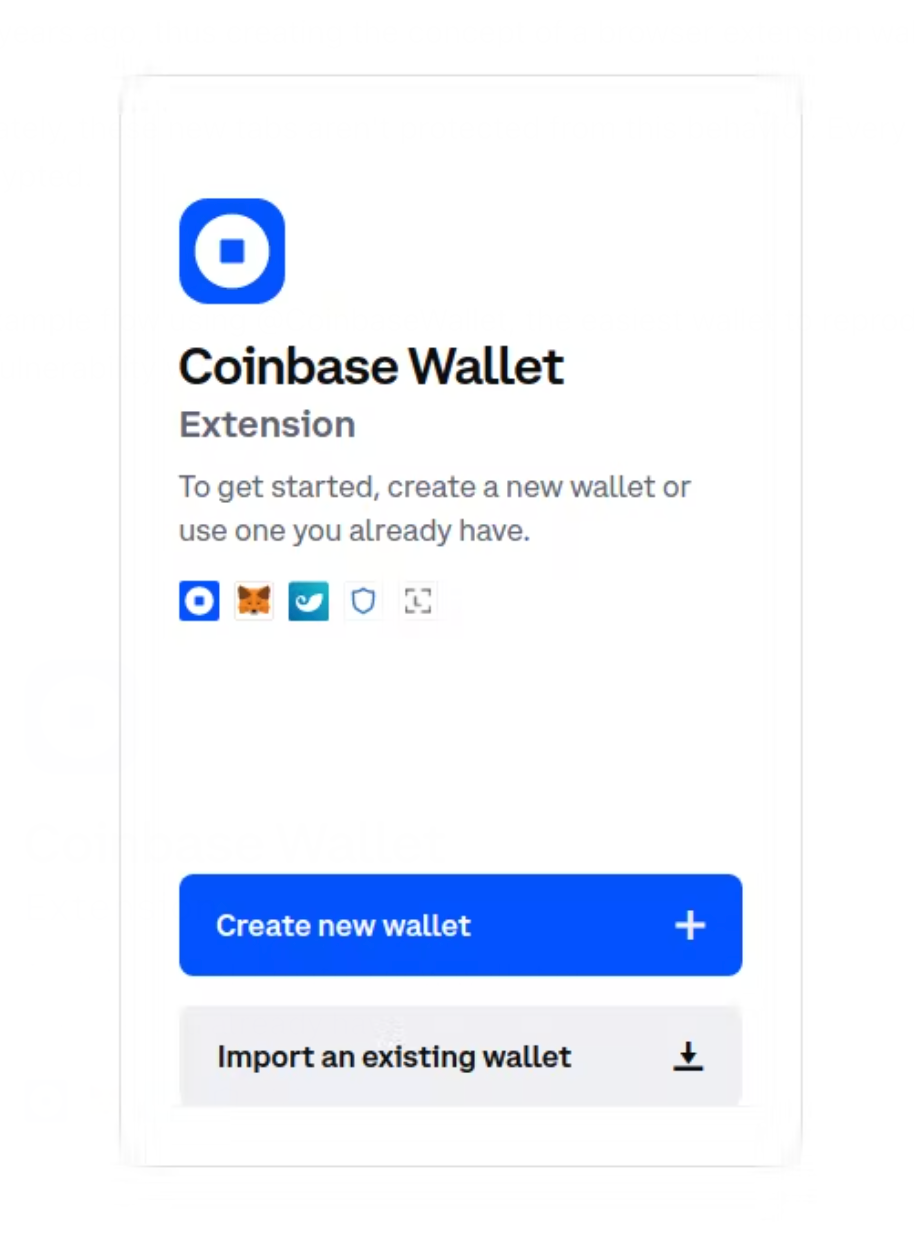
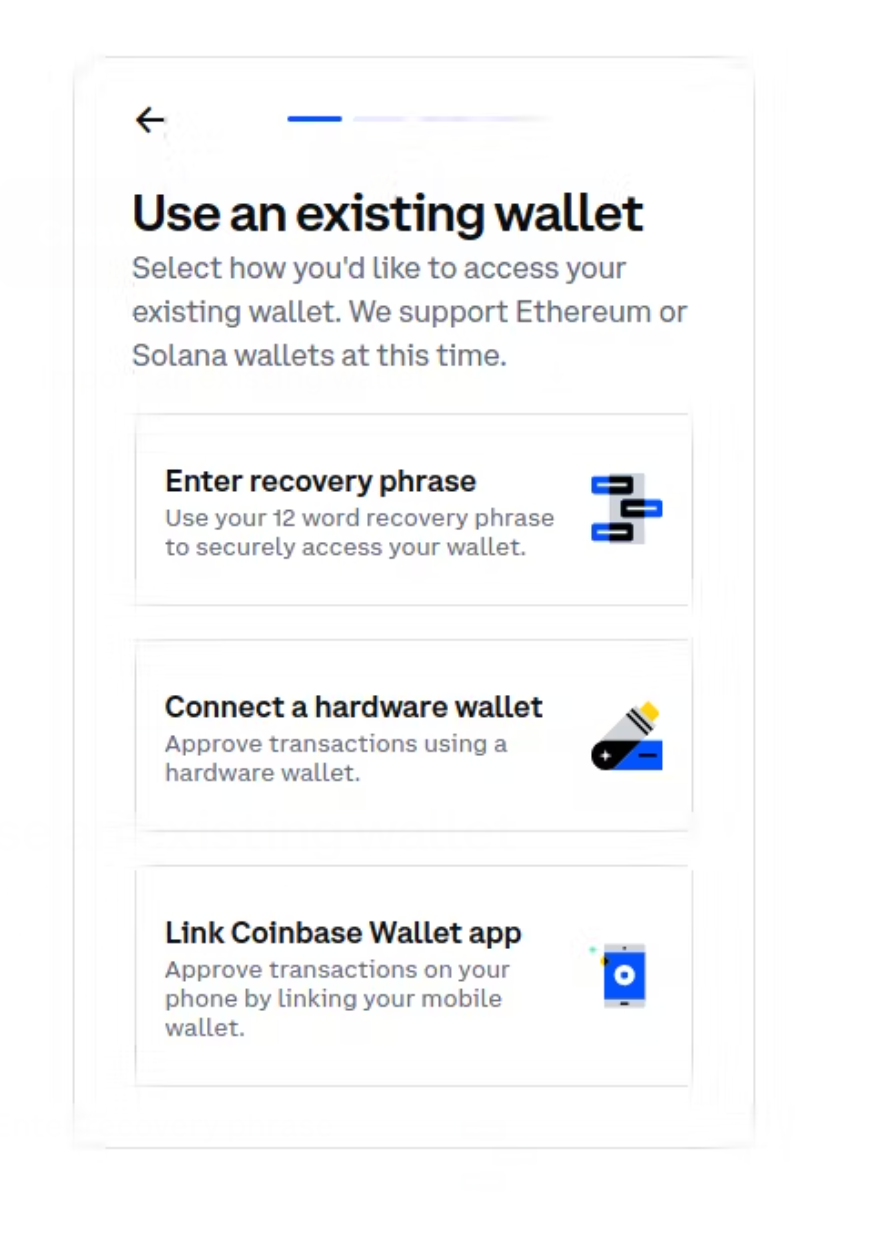
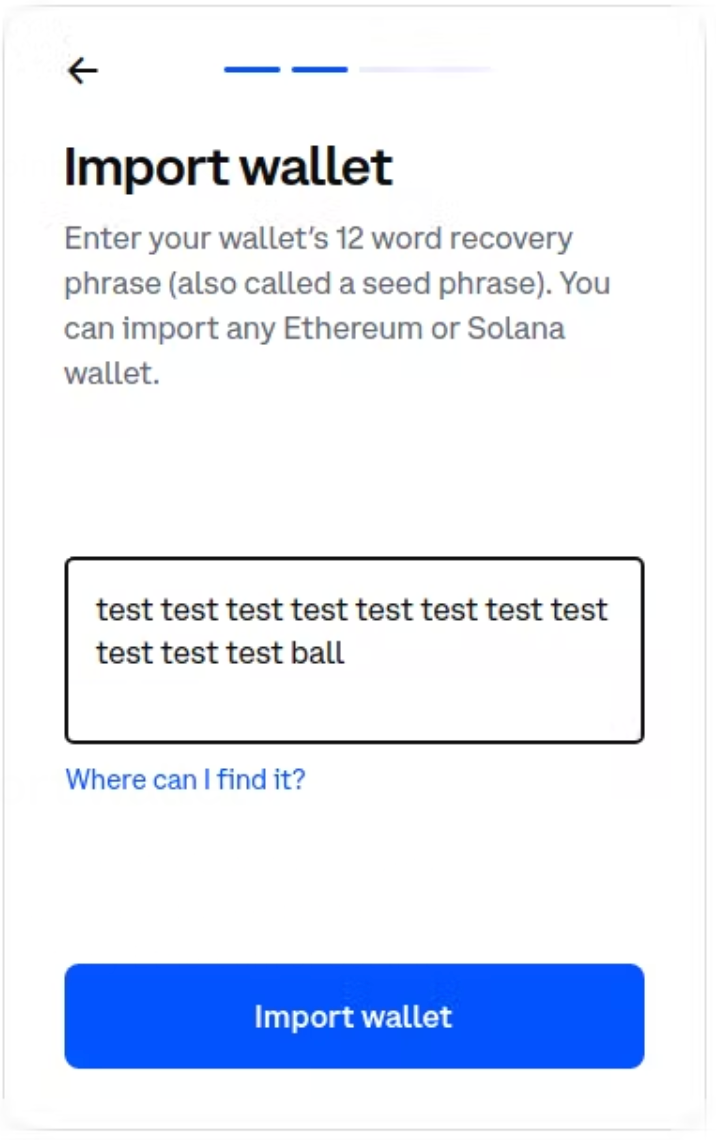
.... And here's a screenshot of this session storage on disk, readable by any other program on your computer. In the middle is your plaintext recovery phrase, easily readable in your favorite text editor.
Variants of this same flow work on older versions of MetaMask, Brave, Phantom, Kepler, and a number of other wallets we’ve tested.
In our testing, this behavior is disabled for browser extension popovers like this.
Securing your Keys 101
So, you're probably shaking in your seat a little. How can you keep yourself safe if you're still using one of these browser wallets?
Here are four things you should do NOW!
- Make sure you're on the latest version of any browser extension wallet you have installed and confirm your wallet vendor has mitigated the issue. For MetaMask, that means 10.12 or later.
- If you've imported a recovery phrase into a vulnerable wallet... your key material was saved to your hard disk, unencrypted, and it might have been exposed to bad actors. You can either live in fear, hoping that wasn't the case, or you can immediately migrate all funds and NFTs to another wallet, using a new recovery phrase.
- If you're storing you're storing a significant amount of funds, consider using a hardware wallet. Many people don't know that you can use a Ledger with MetaMask as well as newer wallets like Tally Ho.
- Consider diversifying funds across different wallets and platforms. This helps avoid monoculture, where tons of funds are at risk from a single announcement like today's.
The Ecosystem Dodged A Bullet
Taylor Monahan, Jordan Spence, Halborn Security, and others from the MetaMask team have done a fantastic job organizing a response across the space, helping wallet developers patch what could have been the largest hack in crypto history.
If you're a wallet dev and unsure if this disclosure impacts you, reach out immediately and we’ll do our best to help pay it forward.
Stay safe out there, frens. 👋

